At a high level, subnets and VLANs are analogous in that they both deal with segmenting or partitioning a portion of the network. However, VLANs are data link layer (OSI layer 2) constructs, while subnets are network layer (OSI layer 3) IP constructs, and they address (no pun intended) different issues on a network. Although it’s a common practice to create a one-to-one relationship between a VLAN and subnet, the fact that they are independent layer 2 and layer 3 constructs adds flexibility when designing a network.
 Subnets (IPv4 implementation)
Subnets (IPv4 implementation)
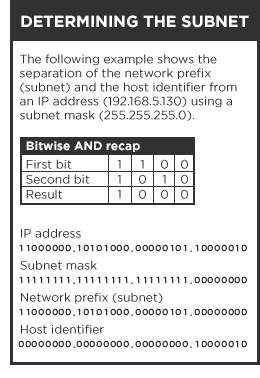
An IP address can be logically split (a.k.a. subnetting) into two parts: a network/routing prefix and a host identifier. Network devices that belong to a subnet share a common network/routing prefix in their IP address. The network prefix is determined by applying a bitwise AND operation between the IP address and subnet mask (typically 255.255.255.0). Using an example address of 192.168.5.130, the network prefix (subnet) is 192.168.5.0, while the host identifier is 0.0.0.130.
Traffic is exchanged or routed between subnetworks via routers (many modern switches also include router functionality) when the routing/subnet prefixes of the source address and the destination address differ. A router constitutes the logical and/or physical boundary between subnets.
The benefits of subnetting a network vary with each deployment scenario. In large organizations or those using Classless Inter-Domain Routing (CIDR), it’s necessary to allocate address space efficiently. It may also enhance routing efficiency, or have advantages in network management when subnetworks are administered by different internal groups. Subnets can be arranged logically in a hierarchical architecture, partitioning an organization’s network address space into a tree-like routing structure.
VLANs
A VLAN has the same attributes as a physical local area network, but it allows for devices to be grouped together more easily, even if they are not connected on the same network switch. Separating ports by VLAN groups separates their traffic in a similar fashion to connecting the devices to a separate, distinct switch of their own. VLANs can provide a very high level of security with great flexibility for a comparatively low cost.
Network architects use VLANs to segment traffic for issues such as scalability, security, and network management. Switches can’t (or at least shouldn’t) bridge IP traffic between VLANs because doing so would violate the integrity of the VLAN broadcast domain, so if one VLAN becomes compromised in some fashion, the remainder of the network will not be impeded. Quality of Service schemes can optimize traffic on VLANs for real-time (VoIP) or low-latency requirements (SAN).
Without VLANs, a switch considers all devices on the switch to be in the same broadcast domain, so VLANs can essentially create multiple layer 3 networks on a single physical infrastructure. For example, if a DHCP server is plugged into a switch it will serve any host on that switch that is configured for DHCP. By using VLANs, the network can be easily split up so some hosts will not use that DHCP server and will obtain link-local addresses, or obtain an address from a different DHCP server.
Additional Thoughts
You can have one physical network and configure two or more logical networks by simply assigning different subnets, like 192.168.0.0 and 192.168.1.0. The problem, though, is that both subnets transmit data through the same switch. Traffic going through the switch can be seen by all other hosts, no matter which subnet they’re on. The result is that security is low and there will be less bandwidth available since all traffic uses the same backbone.
As an alternative, you can create a VLAN for each logical network. Bandwidth availability for each VLAN (or logical network) is no longer shared, and security is improved because the switch that connects each VLAN network (in theory…) will not allow traffic to cross between the VLANs.
Usually VLANs are the better choice for many applications, including audio, but there are times when subnetting makes sense. The main reasons are:
- Mitigating performance problems because LANs can’t scale indefinitely. Excessive broadcasts or flooding of frames to unknown destinations will limit their scale. Either of these conditions can be caused by making a single broadcast domain in an Ethernet LAN too big. Bandwidth exhaustion (unless it’s caused by broadcast packets or flooding of frames) is not typically solved with VLANs and subnetting, though, since they won’t increase the amount of bandwidth available. It usually happens because of a lack of physical connectivity (too few NICs on a server, too few ports in a group, the need to move up to a faster port speed, etc.). The first step is to monitor network traffic and identify trouble spots. Once you know how traffic moves around on your LAN, you can begin to think about subnetting for performance reasons.
- A desire to limit / control traffic moving between hosts at layer 3 or above. If you want to control IP (or TCP, or UDP, etc.) traffic between hosts, rather than attacking the problem at layer 2, you might consider subnetting and adding firewalls / routers with ACLs between the subnets.
For more information, check out the tech notes posted on Cornerstone.
